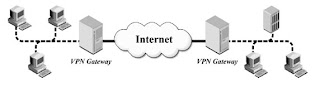
linking two networks through IPSec vpn
The use of virtual private networks VPN client provides several advantages, the most important low cost necessary for its creation, since all that is needed is to use existing Internet and available in advance also as some software protection without the need to extend the wiring.
They also feature a quickly prepared and make advantage of the freedom of movement for the user without the trouble of transferring any hardware. A practical example of the powers that are given to some of the staff where they can achieve their work from locations outside the workplace through connectivity institution or company through a virtual network.
They also feature a quickly prepared and make advantage of the freedom of movement for the user without the trouble of transferring any hardware. A practical example of the powers that are given to some of the staff where they can achieve their work from locations outside the workplace through connectivity institution or company through a virtual network.
The process of linking two networks through IPSec.
The second task is to use IPSec vpn client is to link a user's virtual private network "VPN" in last place through the Internet, as in Figure 3. It is applications, providing virtual network for passengers or employee is located outside of the office to take advantage of network services company details or warehouse stock accounts etcetera.
Applications also give powers to a college student so that access to the university network services regardless of his whereabouts so as to benefit from the contents of a university library or some licensed software that is available exclusively to users from within the University network. In such a case, the user therein case does not have the VPN Gateway.
Applications also give powers to a college student so that access to the university network services regardless of his whereabouts so as to benefit from the contents of a university library or some licensed software that is available exclusively to users from within the University network. In such a case, the user therein case does not have the VPN Gateway.
Simple uses of virtual networks "SSL protocol"
Simplified uses of virtual private network vpn client and the user is familiar SSL protocol where it is known appearance of a picture lock in the browser when you open secured sites. This is commonly used type of virtual private networks in the banks' websites and e mail or electronic gates in the event of the need to provide protection and privacy of communication with the user. SSL protocol is an add code for Internet browsers allow access to the exchange of information locked between the server and the user. Where they are first to issue a certificate for the user before starting to send information.
This certificate contains information encryption system to be used and the date of the permission to use the certificate. After that information is encrypted in the server before it is sent to the user in accordance with the certificate information, which the user will also take him to break the encryption and access to information. Encryption process mentioned provide access to the information of the two parties in the network server and the user .